RSA is an asymmetric algorithm that takes the product of two large primes, p and q called the modulus. Then a number e, which is less than n and prime relative to (p-1)(q-1) is selected. Note that e and (p-1)(q-1) have no common factors except 1. Select another number, d, so that (ed - 1) is divisible by (p-1)(q-1). The values e and d are called the public and private exponents, respectively.
The public key is the pair (n,e); the private key is (n,d). The factors p and q maybe kept with the private key, or destroyed. When a key length is mentioned (for example 768-bit) the number refers to the length of the modulus. Good factors (p and q) should be the same length, so their size is one-half the size of of the key (for a 768-bit key, each is approximately 384 bits).
RSA Technologies owns the patent on RSA, which can be found embedded in Microsoft Windows, Netscape Navigator, Intuit Quicken, Lotus Notes, PGP, and hundreds of other products.
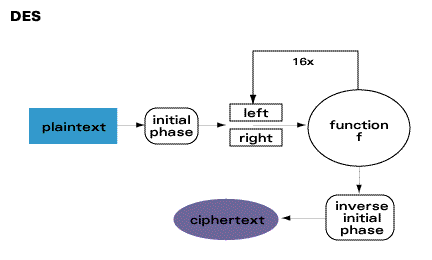
DES is perhaps the most well-know and widely used cryptosystem in the world. It is a symmetric block algorithm written by International Business Machines (IBM) that encodes 64-bit blocks of data using a 56-bit key. After an initial permutation, the data is broken into right and left halves, each 32-bits long. Then 16 rounds of identical operations (called Function F) where the data is combined with the key are performed. After the 16th round, the two halves are joined , and a final permutation (which is the inverse of the initial permutation) is performed.
In 1976, the U.S. Government adopted DES as an official standard for data encryption and has recertified it every five years, however the National Institutes of Standards and Technology (NIST) has indicated that DES may not be recertified again. After the U.S. Government made DES a standard, the American National Standards Institute (ANSI) approved it as a private-sector standard, and DES-based standards and implementations spread quickly through the financial and banking industries. DES has been extensively studied since its publication and is the most well-known and widely used cryptosystem in the world.
DES can be found in both hardware and software implementations.It is common practice to protect a key for DES encryption with triple-DES. The plaintext is, in effect, encrypted three times. A number of modes of triple-encryption have been proposed:
The International Data Encryption Algorithm (IDEA) was formerly known as the Proposed Encryption Standard (PES) and the Improved Proposed Encryption Standard (IPES). IDEA is a symmetric block algorithm that encrypts data in 64-bit blocks with a 128 bit key. The 64-bit data block is divided into four 16-bit sub-blocks, then undergoes eight rounds of operations. In each round, the blocks undergo the XOR algorithm, added and multiplied with one another and with 16-bit sub-blocks from the key. Between each round, the second and third sub-blocks are switched.
Home
Cryptography Defined/A Brief History of Cryptography
Key Length - How Long is Long Enough?
Cryptography in Everyday Life
America's Social/Political Debate
Resources & References